

Inheriti® simplifies data protection through our innovative and patented Secure Share Distribution Protocol (SSDP). Here’s how it works.
Start by creating a data protection plan with Inheriti®.
Your data is then split into shares and encrypted via different algorithms and protocols.
Encrypted shares are distributed across different secure locations or devices, ensuring no central point of failure.
When the time comes, and through a multi-layered verification, beneficiaries can combine their encrypted shares to reveal the secret data securely.
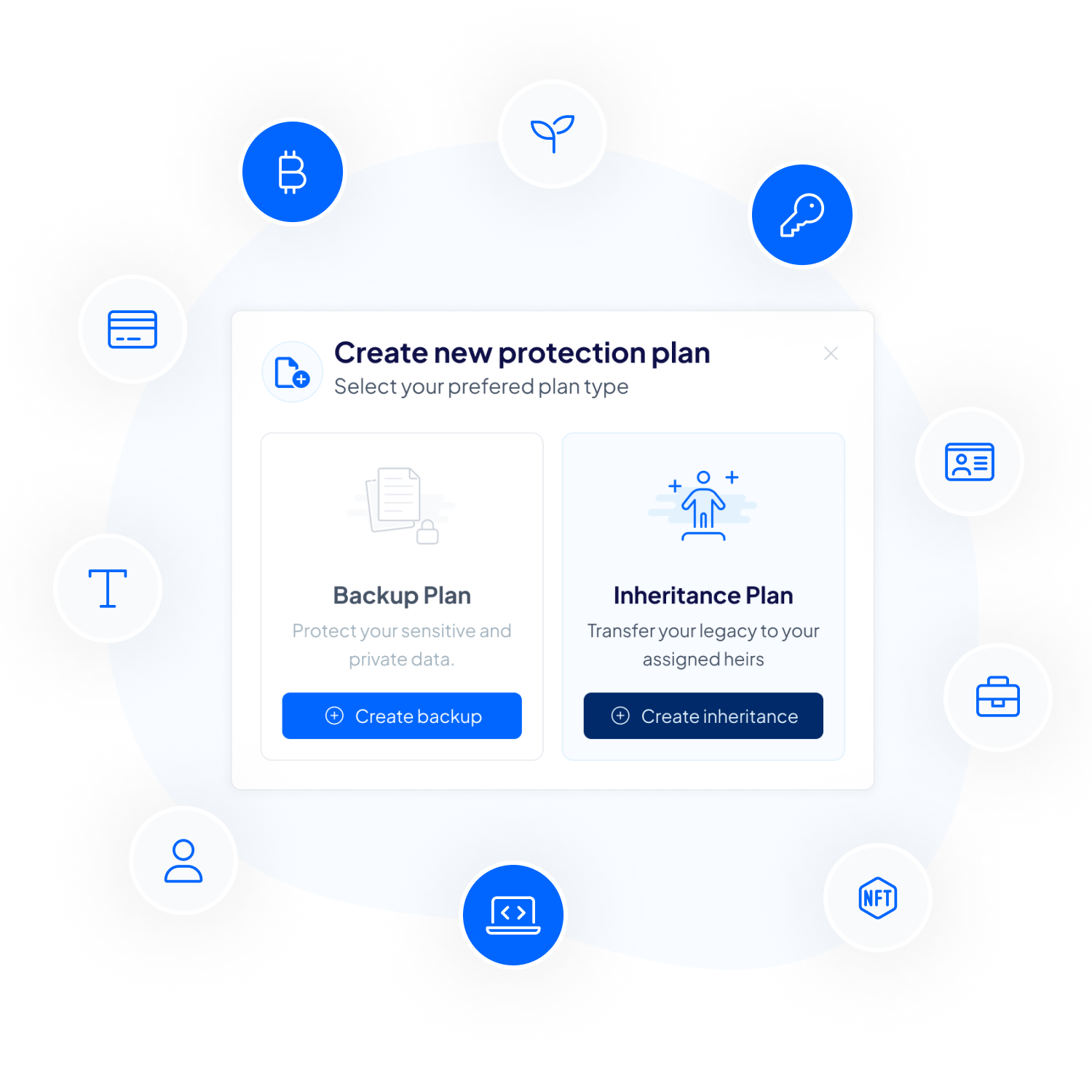
Get started by setting up your customized protection plan. Whether it’s for securing important data or ensuring a smooth inheritance process, just fill in the plan details like:
Your data is always prioritized for security, and will never leave your browser.
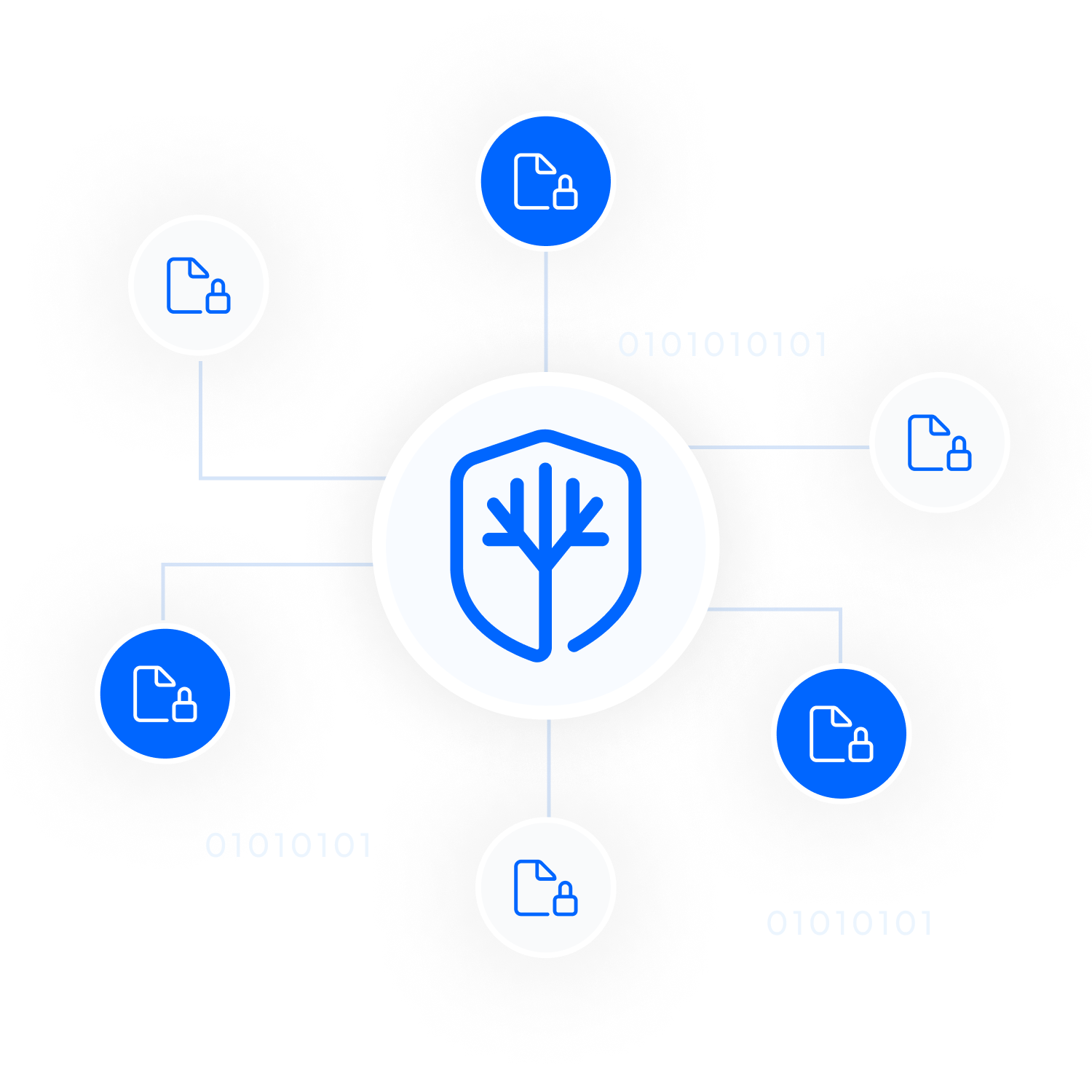
Following the plan setup, your data is first split into separate shares using the Shamir’s Secret Sharing Scheme (SSS). Immediately after splitting, each share is encrypted using the AES-256 algorithm. This dual-step process ensures that each share is independently secure and incomplete on its own, enhancing the data’s overall security.
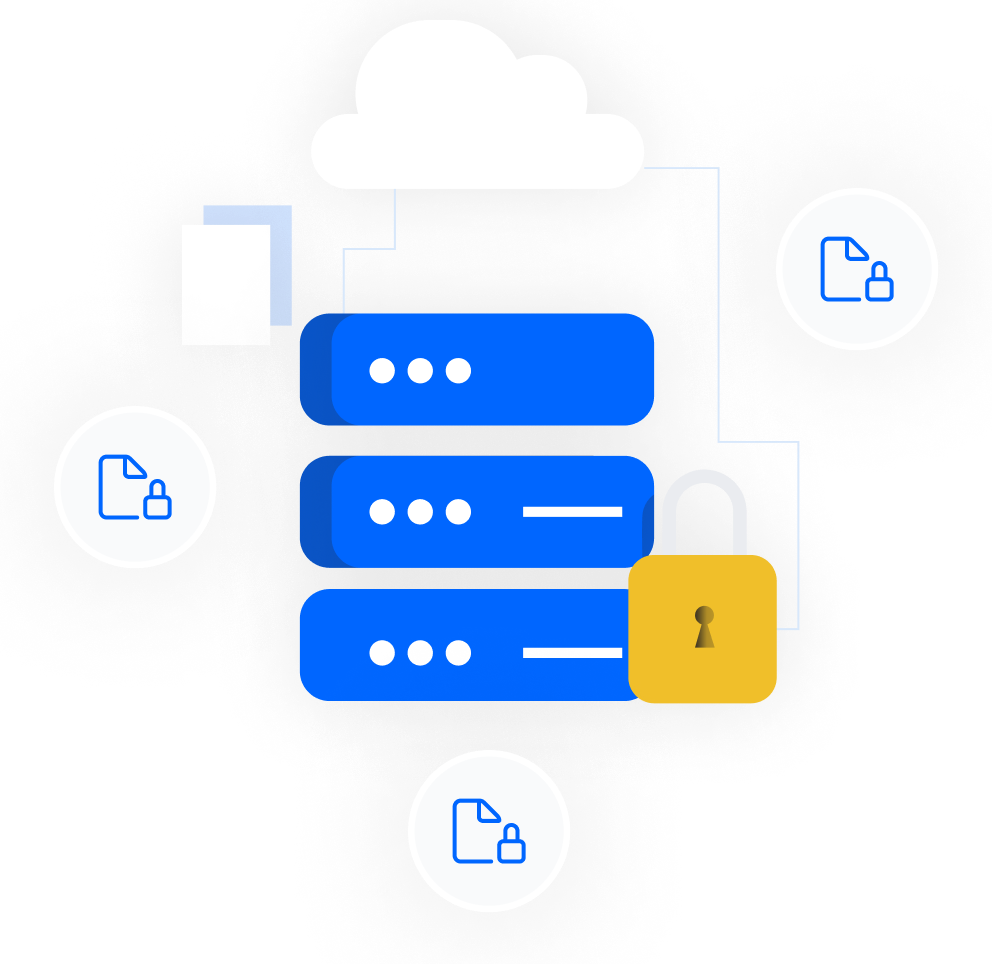
Utilizing our SSDP, the encrypted shares are distributed across various storage layers and devices, such as:
Beneficiaries receive their shares securely and transparently. They can choose to store their shares using SafeKey Pro, a secure cold storage device, or SafeKey Mobile, directly on their mobile phone.
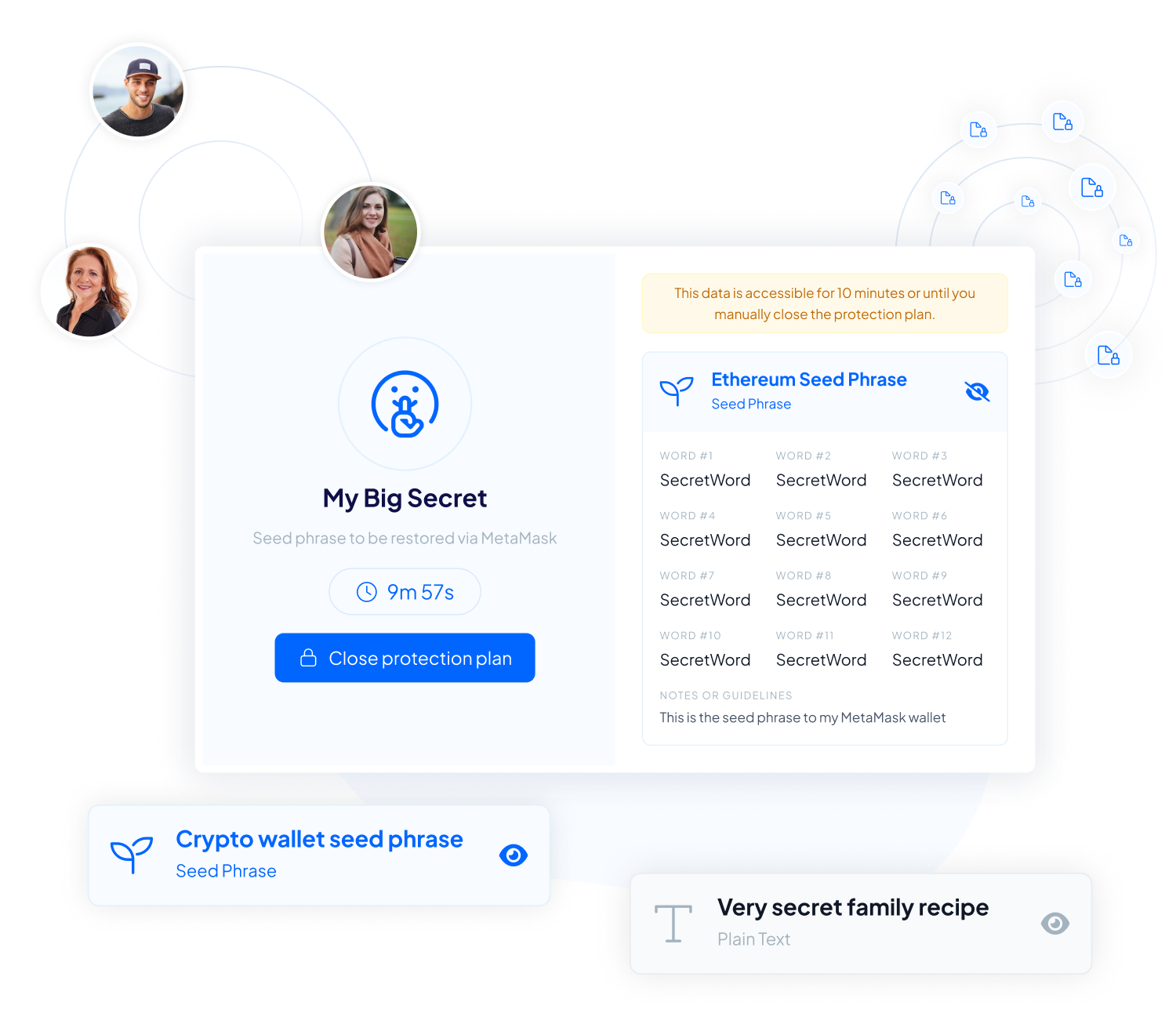
Accessing your data is seamless. After the merge authority initiates the merging process, beneficiaries need to present their shares, activating methods like the Dead Man Switch or Plan Triggers. Your data reconstructs effortlessly when the shares are combined, ensuring access without compromising security and trust.
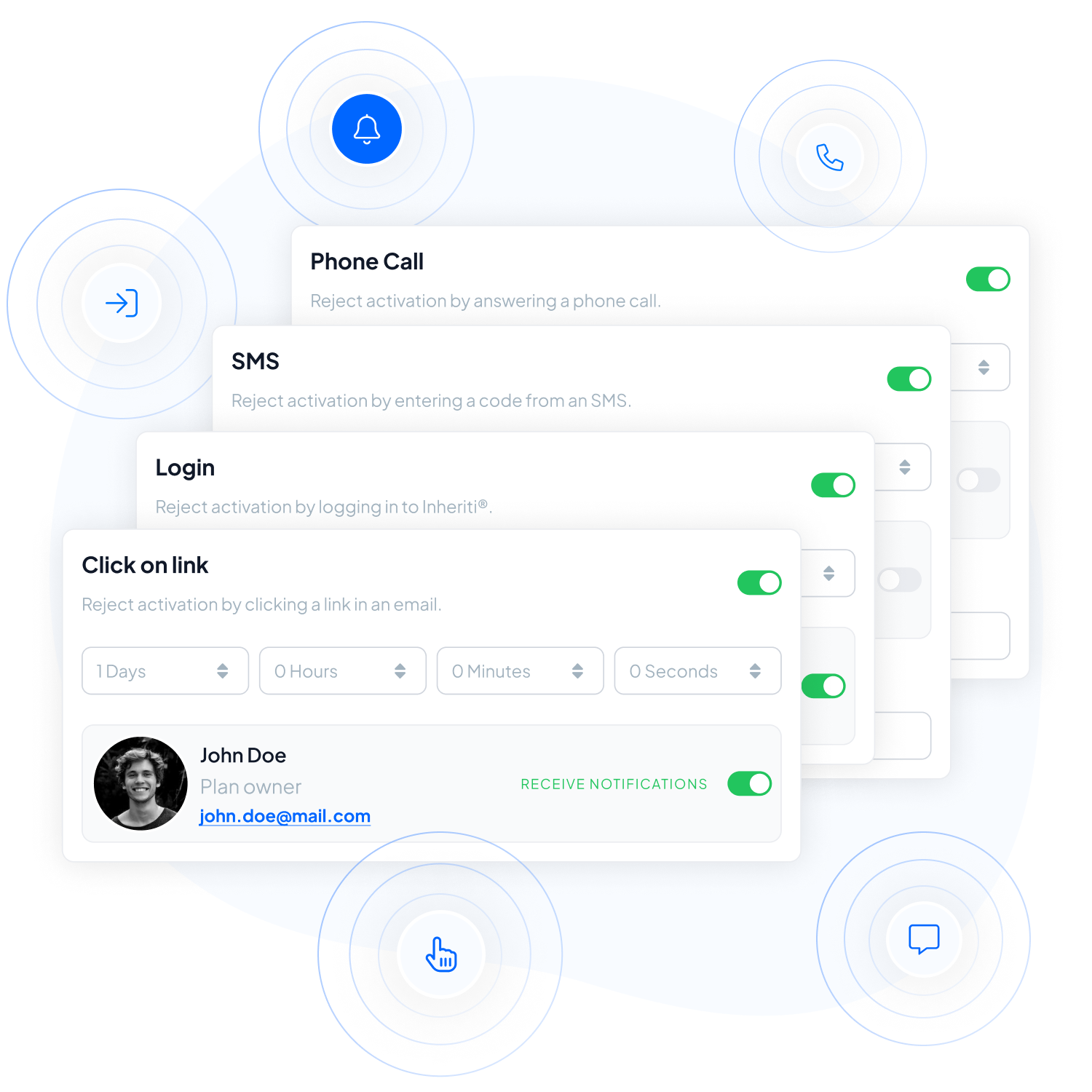
Inheriti® provides additional security layers to enhance data protection, including Plan Triggers and Dead Man Switches:
Dive into the core of Inheriti®’s architecture, where every layer is built with your security and privacy in mind. From advanced encryption protocols to comprehensive audits, discover how we ensure that your digital assets and personal information are protected with unparalleled diligence, providing you with peace of mind in a digital world.
This section aims to address frequently asked questions about how Inheriti® ensures the security and accessibility of your digital assets through our four-step process: Plan Configuration, Split and Encrypt, Distribute, and Merge and Retrieve.
Plan how to secure your digital assets.
Enhancing security through encryption and data fragmentation.
Reconstructing data when necessary.
From precious memories to crucial data and assets, Inheriti® offers both digital inheritance solutions and decentralized data backups. Ensuring your legacy and sensitive data are protected for generations to come.