
Every aspect of Inheriti® is built with security in mind. From the initial design to the final implementation, our solutions are crafted to provide robust protection for your digital assets.
We do not hold any critical or digital asset related information in our databases.
Utilizing military-grade encryption, Inheriti® ensures that your data remains inaccessible to unauthorized users. Your digital assets are encrypted with the same level of security that protects sensitive governmental communications.
Inheriti® adheres to privacy by design principles, ensuring that your personal and financial information is protected at every level of interaction. Our platform is engineered to secure your data while respecting your privacy.
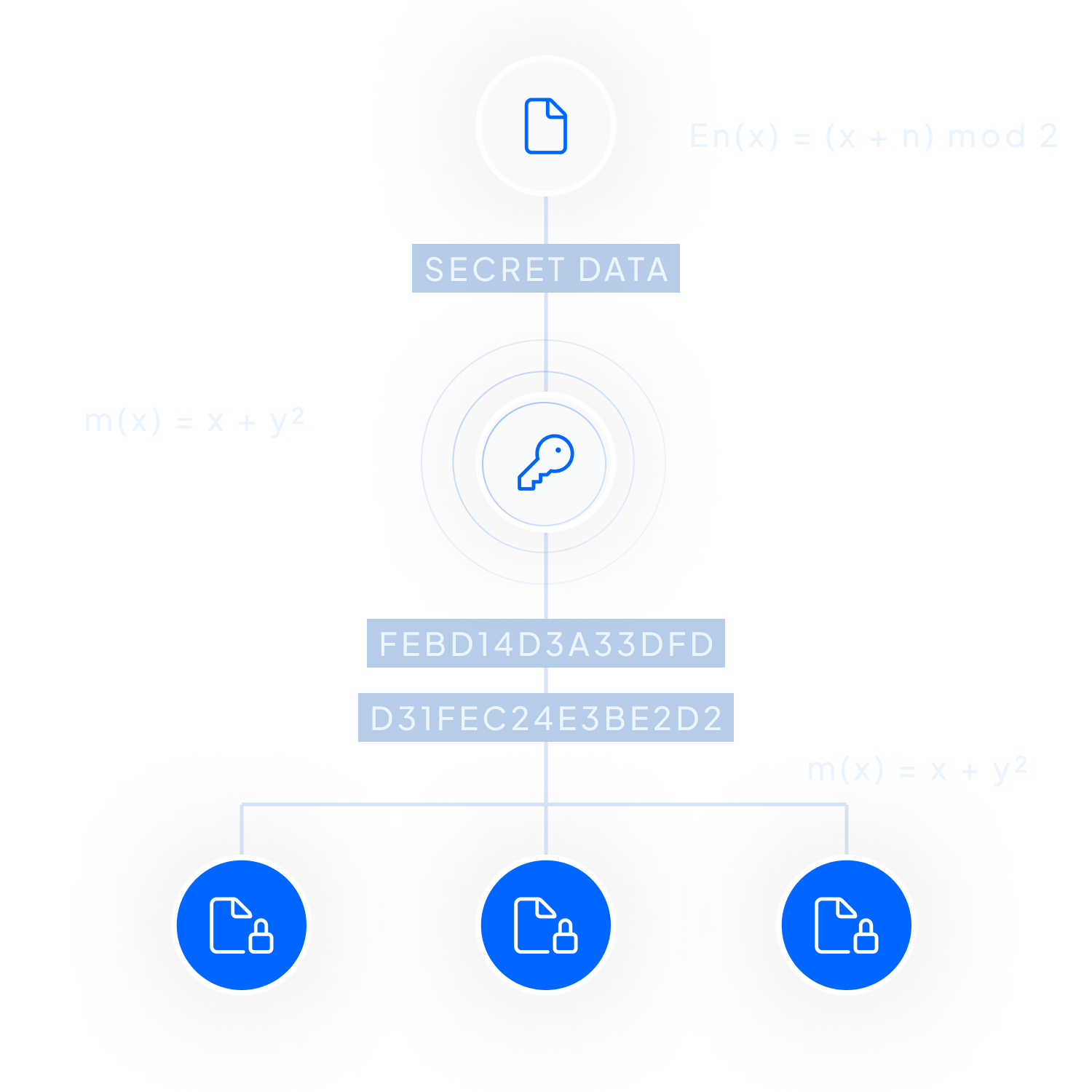
At the core of Inheriti® lies the Secure Share Distribution Protocol (SSDP), a cutting-edge and patented technology engineered to ensure the utmost security and reliability in digital asset management.
SSDP is integral to how Inheriti® protects your digital legacy and sensitive data, setting new standards in the industry for encryption and decentralization.
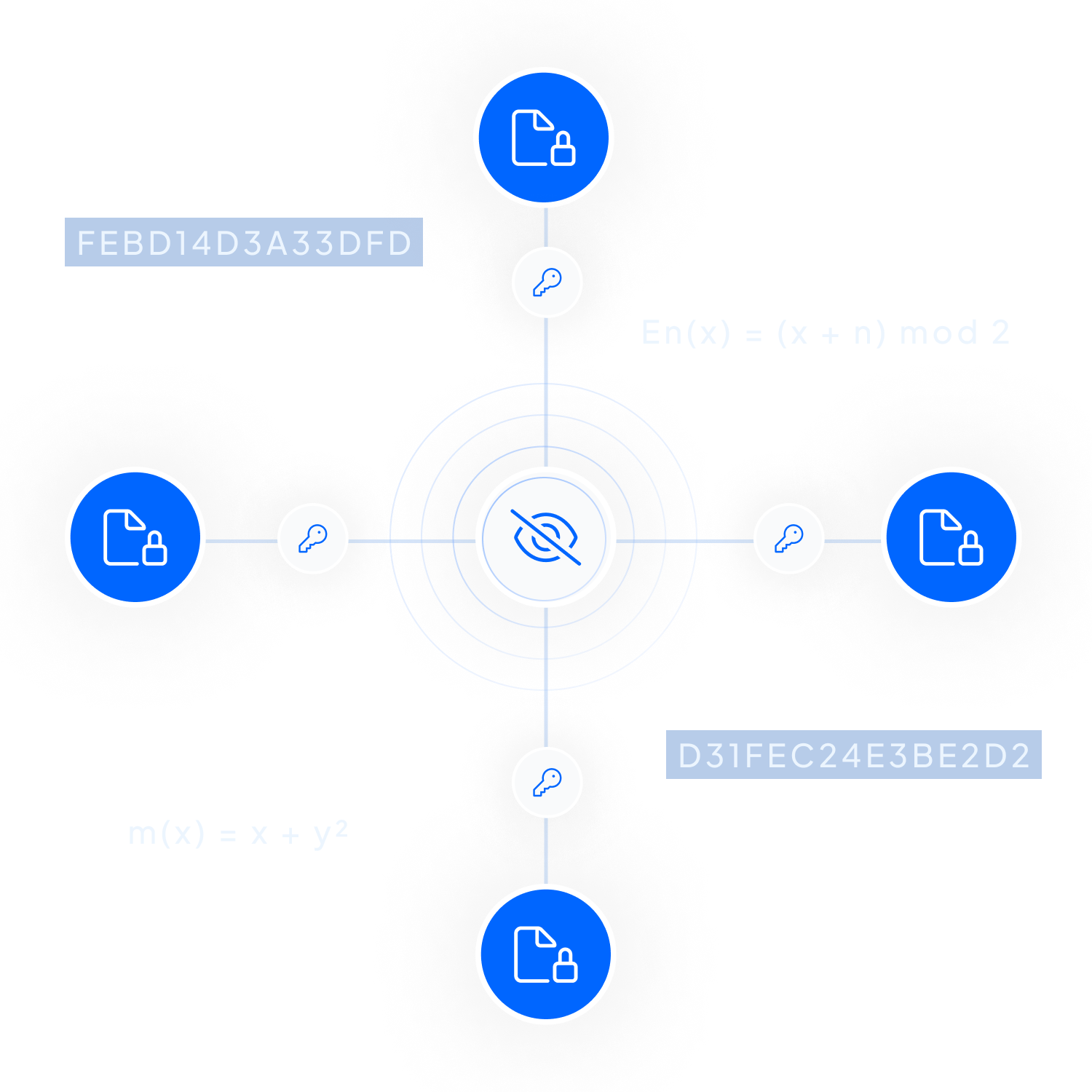
Inheriti® provides tamper-proof data protection, ensuring that once your data is stored, it cannot be altered or accessed without proper authorization.
This level of security guarantees the integrity and confidentiality of your data.

Our protection plans are 100% decentralized, eliminating single points of failure and reducing the risk of centralized data breaches. This decentralized approach enhances the security and reliability of your digital asset protection.

Inheriti® adopts a zero-trust security model, assuming no inherent trust and verifying every transaction. This stringent security measure ensures that only authenticated and authorized users can access your digital assets.
Inheriti® is committed to the highest security standards, evidenced by our extensive audits conducted by Red4Sec. Our smart contracts and the entire Inheriti® platform undergo rigorous evaluations, including white-box penetration tests on our JavaScript libraries, SDKs, source code, and APIs.
These audits ensure that every component of Inheriti® upholds exceptional security, safeguarding user data and maintaining the integrity of our digital legacy protection services.
From precious memories to crucial data and assets, Inheriti® offers both digital inheritance solutions and decentralized data backups. Ensuring your legacy and sensitive data are protected for generations to come.