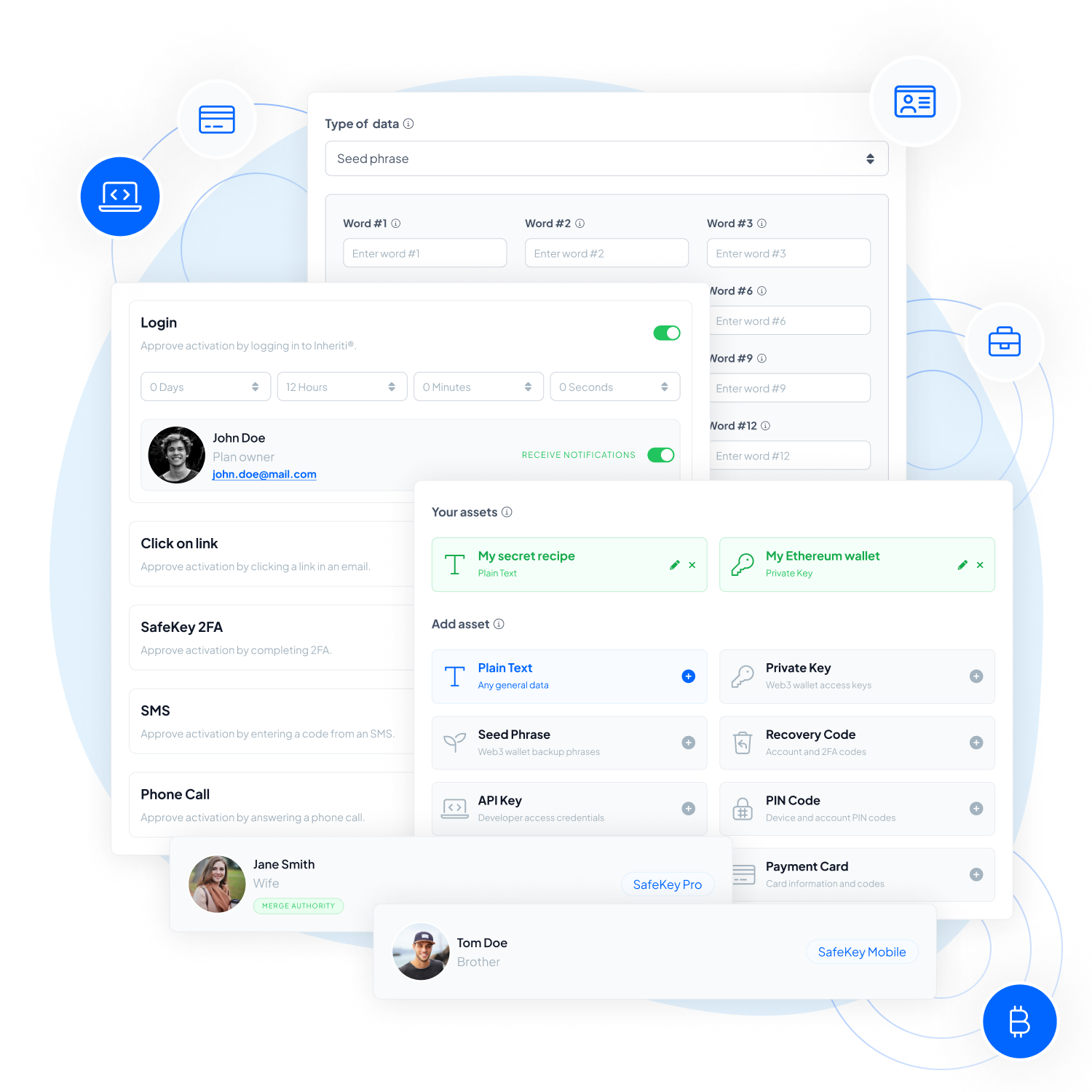

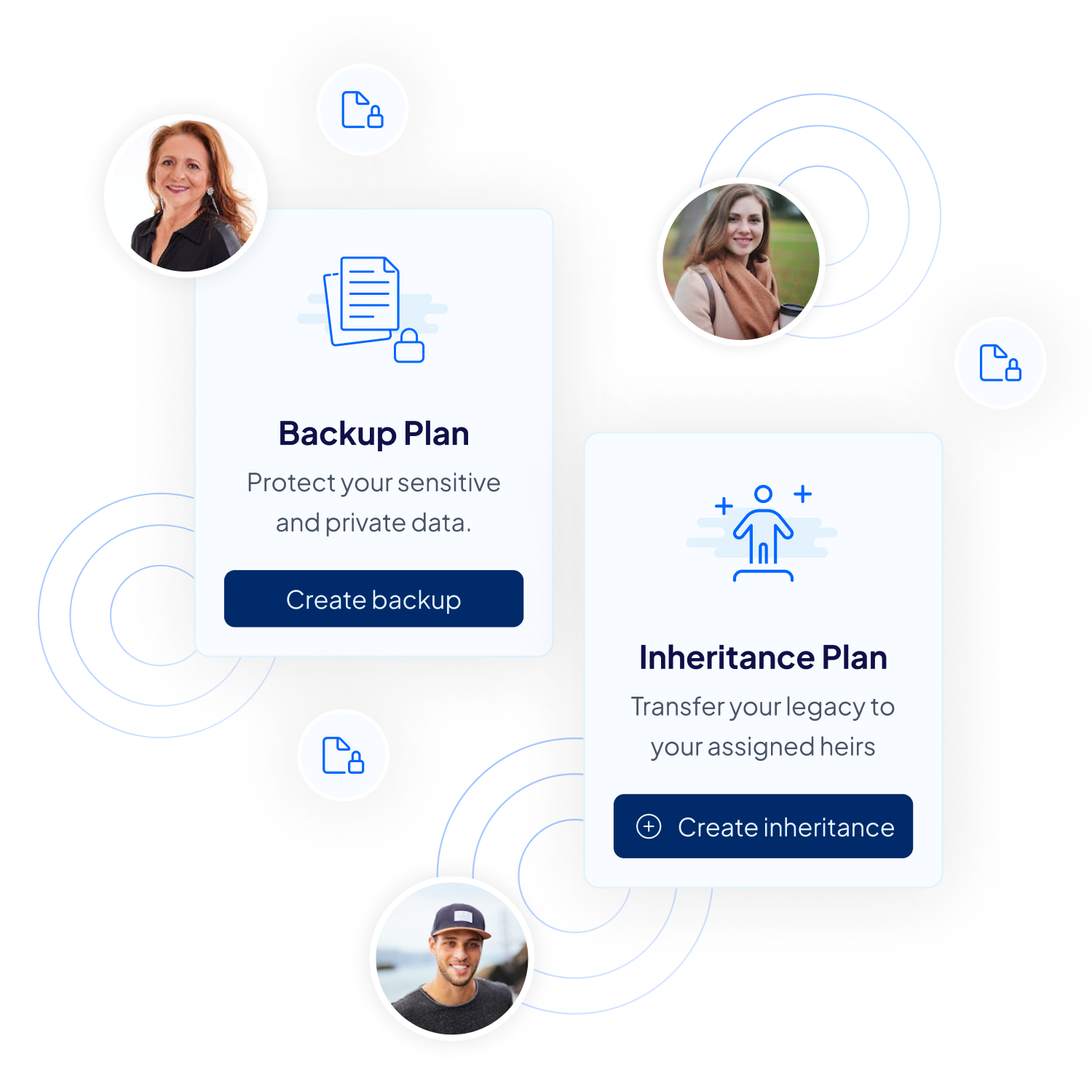
A Protection Plan refers to a secure and decentralized method for users to safeguard their data in an encrypted manner.
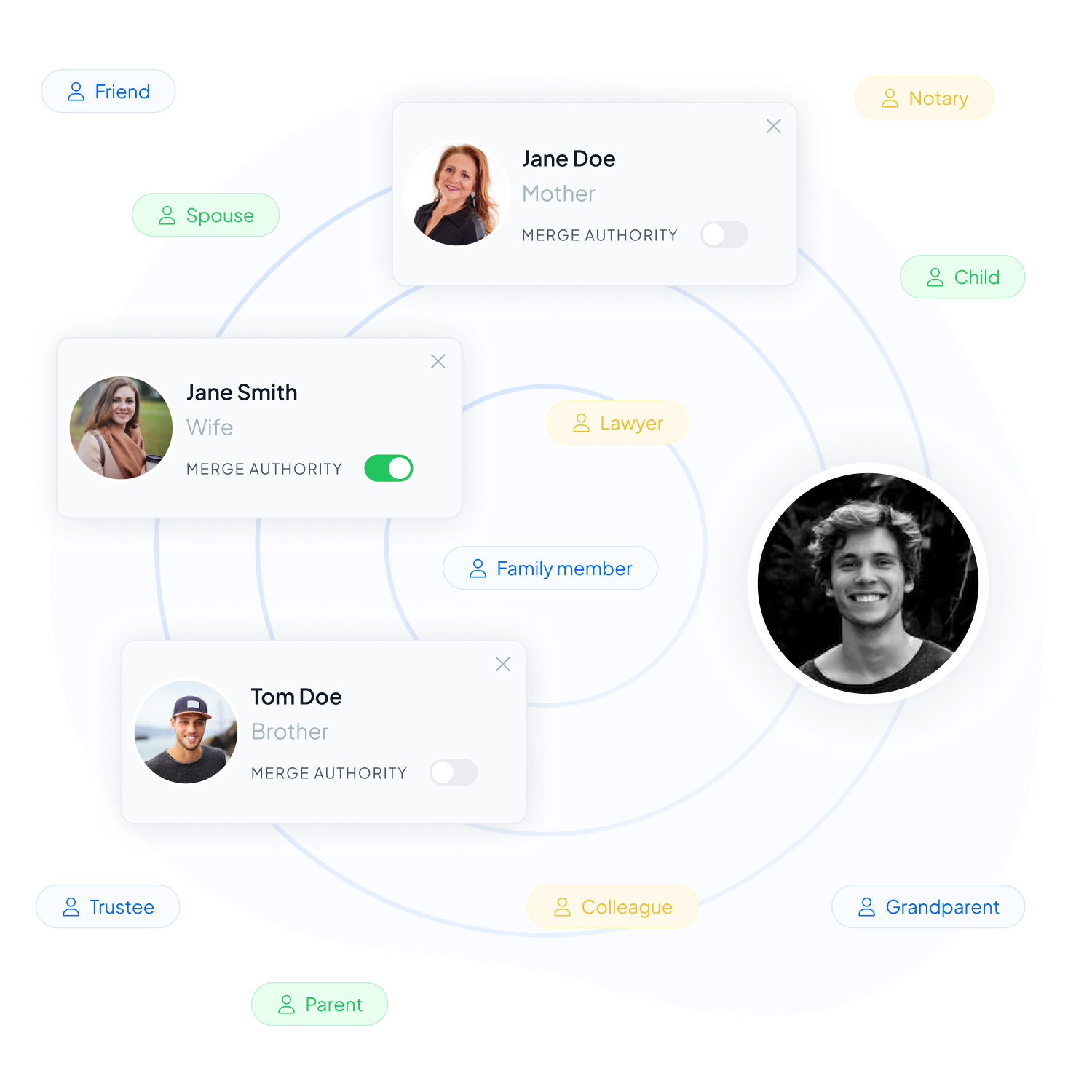
Beneficiary is an overarching term used to refer to all individuals who hold shares of a protection plan. It encompasses Shareholders, Heirs, and other designated individuals who are entitled to receive the benefits or assets specified in the plan.
Plan shares are created for each beneficiary in pairs. These shares contain encrypted and split portions of the secret data. Each beneficiary receives at least two plan shares, allowing them to collectively access and recover the protected data.

Activation Method is the overarching term used to describe the methods employed within protection plans to initiate specific actions or events. It encompasses the Dead Man Switch and Plan Trigger, which are two common activation methods utilized in different types of plans.
The Plan Trigger is an activation method employed in various protection plans, particularly in backup plans. It acts as a security feature to verify the owner’s agreement for the data to be opened.
The Dead Man Switch is an activation method used in certain protection plans, particularly in inheritance plans. It serves as a verification mechanism to confirm the status of the plan owner and gets triggered if a required action is not taken before the configured timer hit 0.
Our unique decentralized storage mechanism ensures that your data isn’t just encrypted and fragmented, but it’s also stored across multiple layers, making unauthorized access exponentially harder. Instead of placing all your valuables in a single safe, it’s like distributing them across multiple safes, each with its own security protocols.
SafeKey Pro has been designed with custom internal storage. This allows you to cold store encrypted shares of your protection plans.

SafeKey Mobile is the mobile alternative to the internal custom storage of SafeKey Pro devices and is connected to your SafeID account.

Safe and reliable cloud solution for securely storing mobile shares for a limited period. With advanced encryption and robust security measures, mobile shares are safeguarded until beneficiaries are ready to claim them.
Using the strength of distributed ledger or blockchain technology, your validator and backup shares are kept safe from anyone trying to open protection plans without permission. Blockchain’s design, where no one central entity can change things once they’re recorded, ensures that protection plans are kept safe and genuine.
Inheriti®’s merging process prioritizes data security. It begins when the Merge Authority (MA) connects their SafeKey device, prompting Inheriti® to scan for linked plan shares. If multiple plans are found, the MA chooses one. The system confirms the MA’s authenticity and checks the activation methods like the Dead Man Switch.
If the owner doesn’t respond, it’s assumed they approve of or are no longer available. All remaining beneficiaries’ SafeKeys (either SafeKey Pro or SafeKey Mobile) are then used to decrypt plan shares.
Finally, Inheriti® merges these shares, revealing the original data.
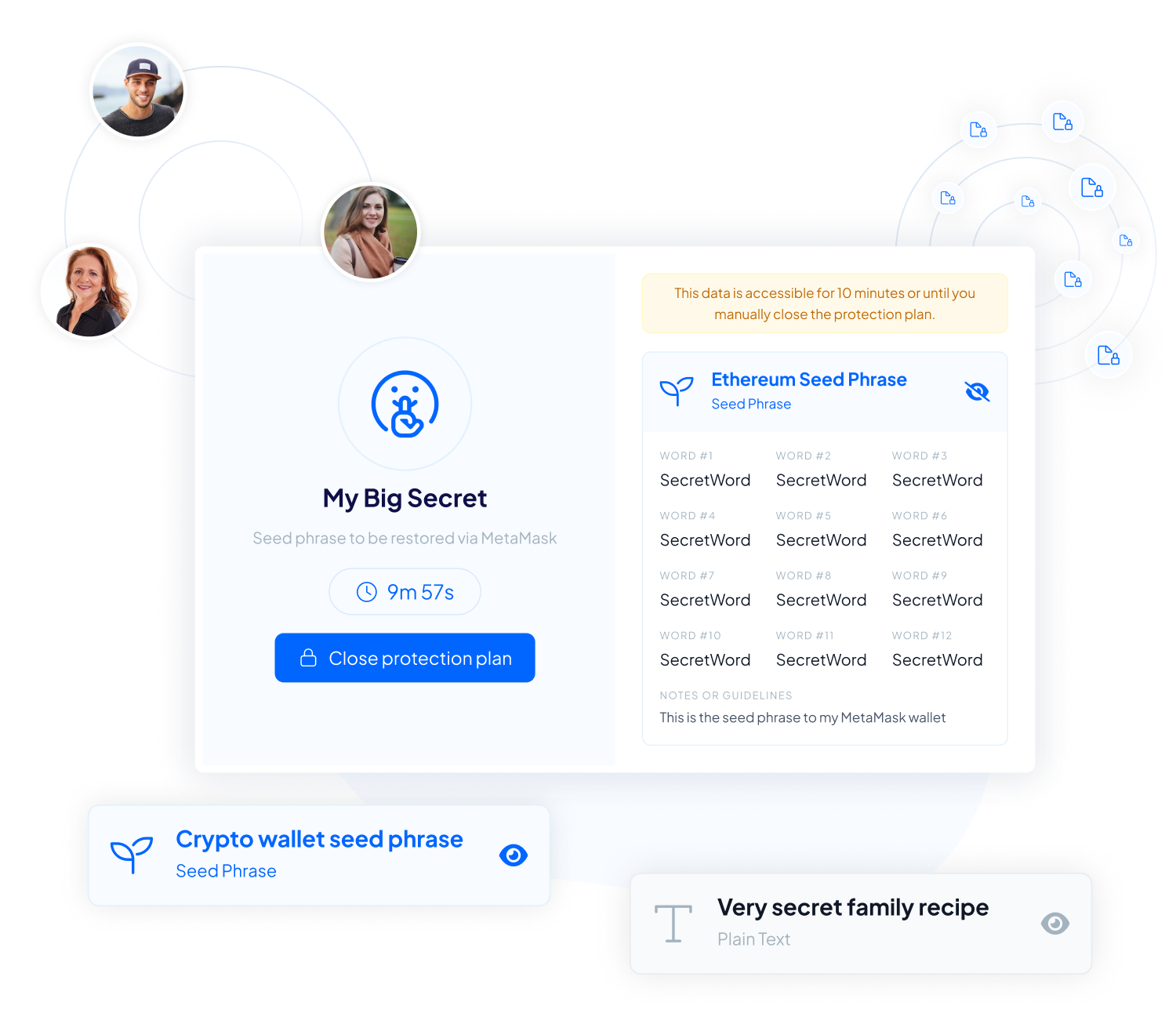
From precious memories to crucial data and assets, Inheriti® offers both digital inheritance solutions and decentralized data backups. Ensuring your legacy and sensitive data are protected for generations to come.