
Still using paper to store your passwords or important data? Paper is vulnerable to theft, loss, and damage — not to mention easily readable by anyone who comes across it.
Inheriti® replaces risky paper storage with secure, encrypted decentralized storage, ensuring that your secret data is protected against all physical dangers, single points-of-failure, and remains private.

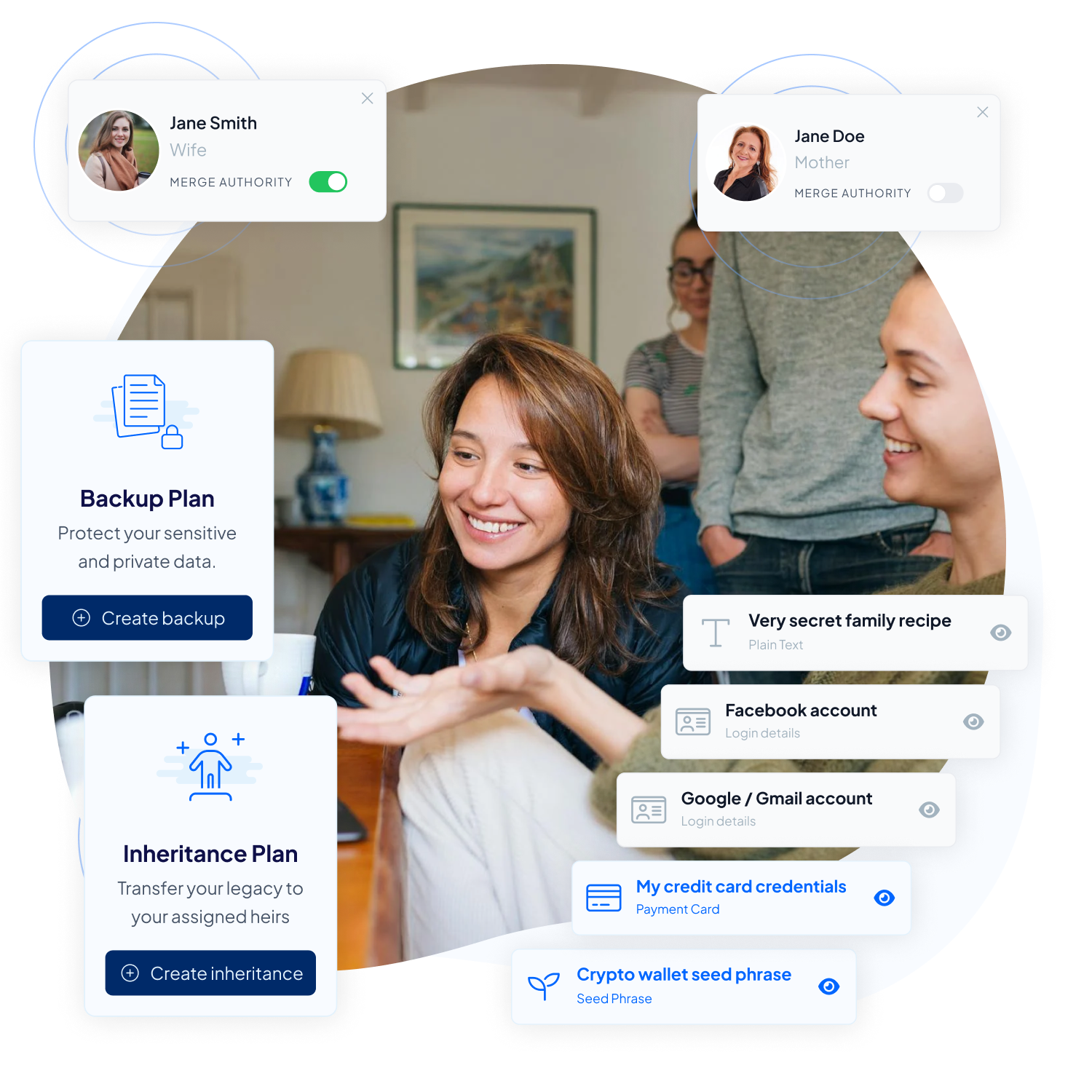
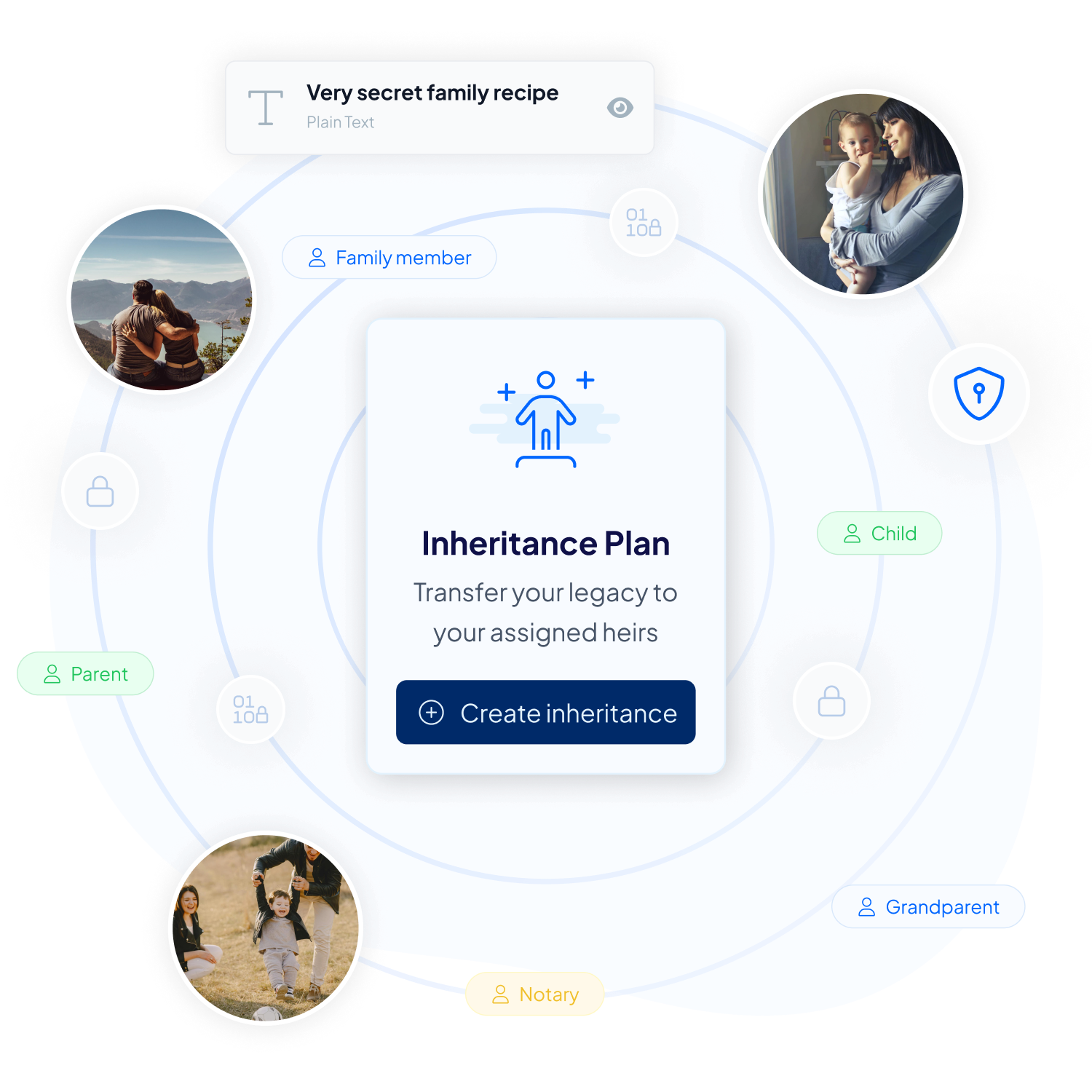
Are you worried about the fair distribution of your digital assets after you’re gone? Traditional inheritance can sometimes lead to disputes or mismanagement, especially if one heir tries to outmaneuver others.
Inheriti® uses security mechanisms like the Dead Man Switch to ensure that your secret data is accessed exactly as and when you intend, without the possibility of interference. This way, you maintain control over your assets, ensuring they are passed on appropriately, even if you’re dead.
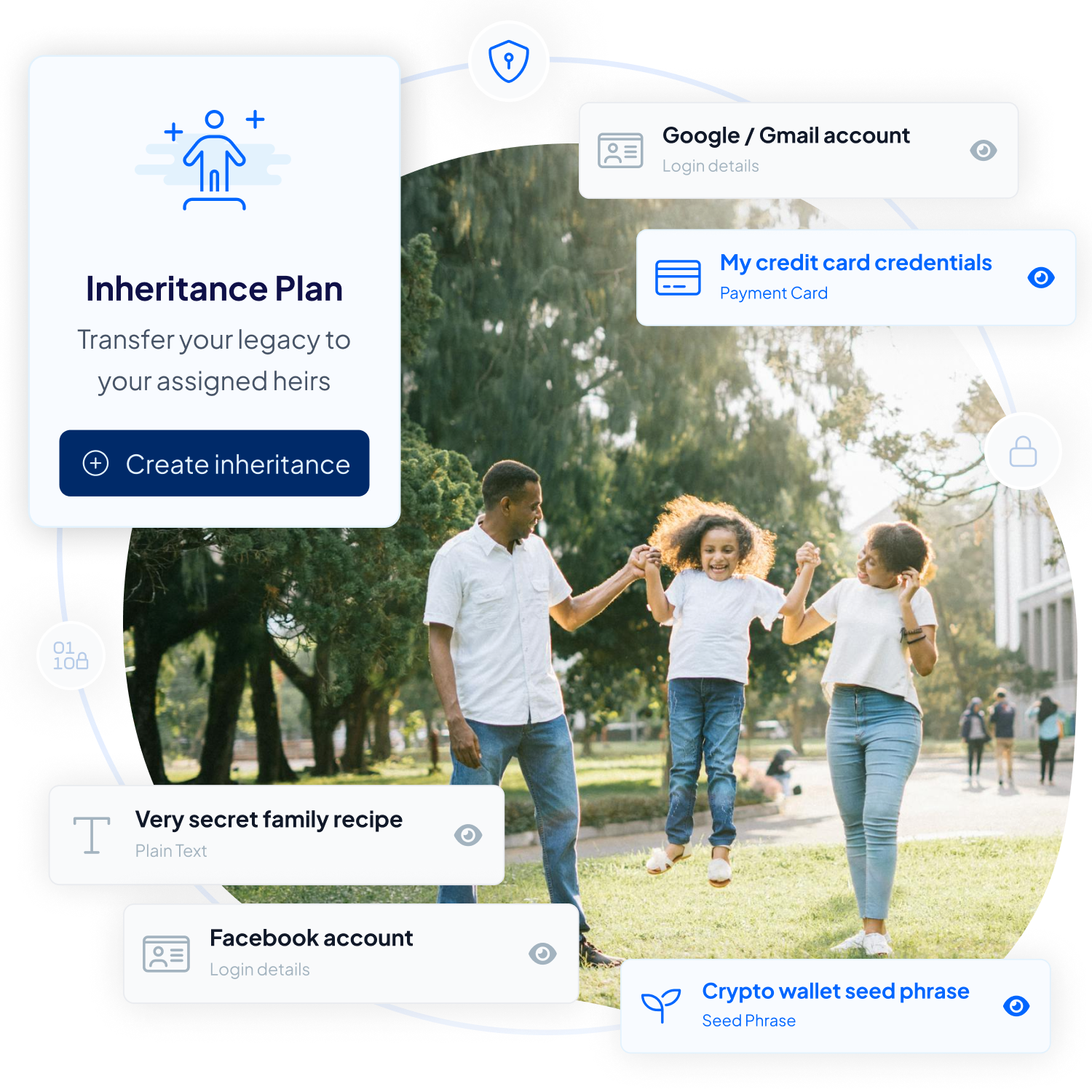
Dealing with the inheritance of digital assets and online accounts doesn’t have to be complex or breach your privacy. Traditional methods often involve lengthy legal processes and lack discretion, potentially exposing your plans to unwanted parties.
Inheriti® streamlines the digital inheritance process, offering clear, customizable, and private protection plans that bypass intermediaries. This ensures your digital assets are handled swiftly and according to your precise wishes.
Relying on centralized third-party cloud services to store your sensitive data? These platforms can become targets for hackers and often lack sufficient security for critical information.
Inheriti® uses decentralized storage solutions to distribute encrypted shares of your data securely across multiple layers, reducing the risk of data breaches and unauthorized access.
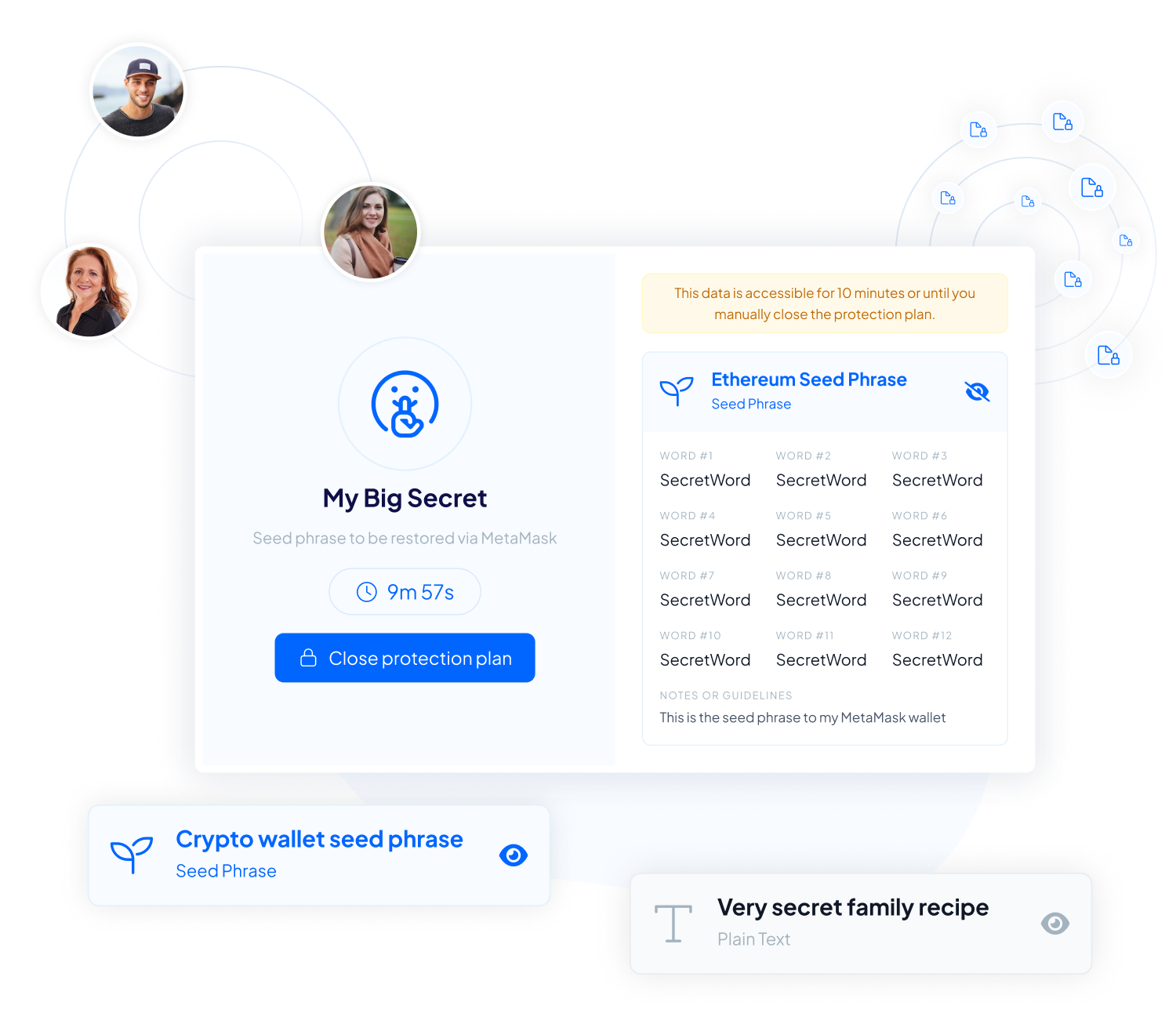
Do you still store important data and passwords in documents on your computer or external hard drives? Local storage devices are susceptible to hacking, physical damage, and loss.
Inheriti® safeguards your digital assets by encrypting them and storing them in secure, decentralized locations, far beyond the reach of local device failures or cyber threats.

Worried about unauthorized access to your written data or unencrypted files? Without proper security measures, anyone who accesses your device can read or steal your information.
Inheriti® encrypts and splits your data into shares, making it impossible for unauthorized users to reconstruct or understand your data without the necessary permissions or shares.
Concerned about the privacy of your data with notaries or lawyers? Even when using trusted third parties, your unencrypted documents and sensitive information are visible to them.
Inheriti® ensures total privacy by encrypting your data so that no one, not even Inheriti®, can access or read your information without your explicit permission and without collecting the other shares.
What happens if you forget your login details or lose access to digital accounts? Such scenarios can be distressing, potentially leading to the irreversible loss of digital assets.
Inheriti® mitigates these risks with robust encrypted backup solutions that ensure you, or designated individuals, can recover access swiftly and securely, no matter the circumstances.